Thousands of businesses across the globe save time and money with Okta. Find out what the impact of identity could be for your organization.
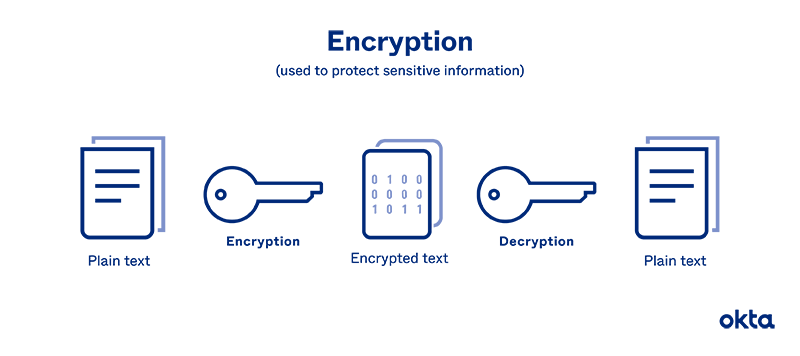
Encryption scrambles your password so it's unreadable and/or unusable by hackers. That simple step protects your password while it's sitting in a server, and it offers more protection as your password zooms across the internet.
Imagine that you've created the strongest password possible. Now, imagine that all of your hard work is stored in plain text on your company's server. If a hacker gets inside, what happens next? All of your efforts go to waste, and your username and password are sold on the open market to the highest bidder.

Problems like this are common. In 2020, for example, security advocates discovered that unprotected usernames and passwords were sent to servers in China from internet-enabled doorbell systems.
Experts use terms like salt, SHA-1, and private key to describe what encryption is and how it works. The terminology can be intimidating, especially for people with no background in computer science.
But put plainly, password encryption works by putting your original word through a series of scrambling steps.
Four main types of encryption exist.
No matter how your company handles encryption, the result is the same. Your password changes from something you know and can remember into something that looks completely random.
Understanding password safety is a bit like learning a new language. Several tools exist to transform your passwords, and they all work a bit differently.
Imagine that our password is R@nT4g*Ne! (Rent Forgone, in common terminology.) Let's pass this through several different encryption tools:
A persistent hacker can jump through your defenses and access your files. But use systems like this, and you're likely to cause significant delays. Hackers grow frustrated when they can't discover the algorithms you use to protect passwords. They may choose a different target instead.
With the use of hashing codes and salt, you can protect your password at rest and in transit. But you won't achieve full security until you do a little bit more. In fact, experts say that a strong encryption policy can leave you with blind spots. You think you're secure when you're not.
Be an advocate for strong password policies. Ensure that yours are:
If you're notified of a breach, take action right away. The longer you delay, the more time a hacker has to steal data, take over your system, or both.
We build secure authenticationsecurity systems for companies both large and small. We can secure your information, data, and ensure privacy with advanced password management and multi-factor authentication solutions that will leave hackers scratching their heads.
We'd love to tell you more about how this works and how you can apply it. Contact us to find out more.
Creating Strong Passwords. (October 2018). Surveillance Self-Defense.